Wireless network implementation management security
 The Cisco Unified Wireless Network features a comprehensive architecture of security tools and technologies to secure the WLAN environment, clients, and infrastructure, which are summarized in Chapter 4, "Cisco Unified Wireless Network Architecture— Base Security Features" of the Wireless and Network Security Integration Design Guide. In a comprehensive, network-wide layered security solution, the Cisco Unified Wireless Network plays an important role in securing wireless access, but there are opportunities to create a superset of layered network security via collaboration with the network infrastructure.
The Cisco Unified Wireless Network features a comprehensive architecture of security tools and technologies to secure the WLAN environment, clients, and infrastructure, which are summarized in Chapter 4, "Cisco Unified Wireless Network Architecture— Base Security Features" of the Wireless and Network Security Integration Design Guide. In a comprehensive, network-wide layered security solution, the Cisco Unified Wireless Network plays an important role in securing wireless access, but there are opportunities to create a superset of layered network security via collaboration with the network infrastructure.
A wireless network is only one of the attack vectors against a network. While a WLAN network must be secure and able to protect itself from attack, a network-wide security solution that only addresses WLAN-related attacks is dangerously unbalanced. Mobile network clients need to be protected on all interfaces at all locations, enterprise networks need to be protected on all their perimeters, and monitoring and anomaly detection are required regardless of the source of network traffic. Ideally the same sets of tools and interfaces should be used to provide these baseline security functions as it reduces operational costs, reduces the risk of misconfiguration, and avoids the creation of a unbalanced security architecture that can be simply bypassed.
illustrates the role of the Cisco Unified Wireless Network security and the roles of other components in a network security architecture.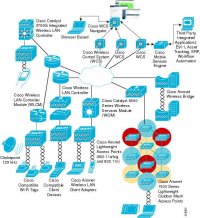 The Cisco Unified Wireless Network provides solutions and WLAN standards-based proactive and operational security, and components such as Cisco Security Agent (CSA), Cisco Network Access Control (NAC) Appliance, Cisco Intrusion Prevention System (IPS), Cisco Security Monitoring, Analysis and Response System (CS-MARS), and Cisco firewalls build on this to provide an overall network security architecture. This provides a layered security system where the Cisco Unified Wireless Network provides security particular to the access layer technology and integration into the overall network security system.
The Cisco Unified Wireless Network provides solutions and WLAN standards-based proactive and operational security, and components such as Cisco Security Agent (CSA), Cisco Network Access Control (NAC) Appliance, Cisco Intrusion Prevention System (IPS), Cisco Security Monitoring, Analysis and Response System (CS-MARS), and Cisco firewalls build on this to provide an overall network security architecture. This provides a layered security system where the Cisco Unified Wireless Network provides security particular to the access layer technology and integration into the overall network security system.
Table 1 WLAN Security Elements and General Network Security Elements
You might also like
Lessons from China — The Hindu
Transferring the project appraisal function and the erstwhile Planning Commission staff to line ministries would be good moves. ..
Modi's Japan visit 2014: PM has lifted Japanese mood for business with India .. — Economic Times
He promised to broad-base the kind of welcoming environment that Japanese investors have found in Gujarat and announced the setting up of a "Japan Plus Management Team" in the PMO. He also proposed that Japanese ..
State continues suicide prevention efforts — The Sheridan Press
In July, the WDH released an updated “Preventing Suicide in Wyoming” plan, which was unveiled publically last week at the Wyoming Suicide Prevention Summit in Casper and will be implemented statewide over the next two years. .. Dr.
Operations and IT Graduate Trainee — TARGETjobs
For the business to continue to grow and develop in a scalable way, the right processes, systems and technologies need to be in place – Operations and IT drives their improvement, development and implementation. Operations and IT strives to ..






